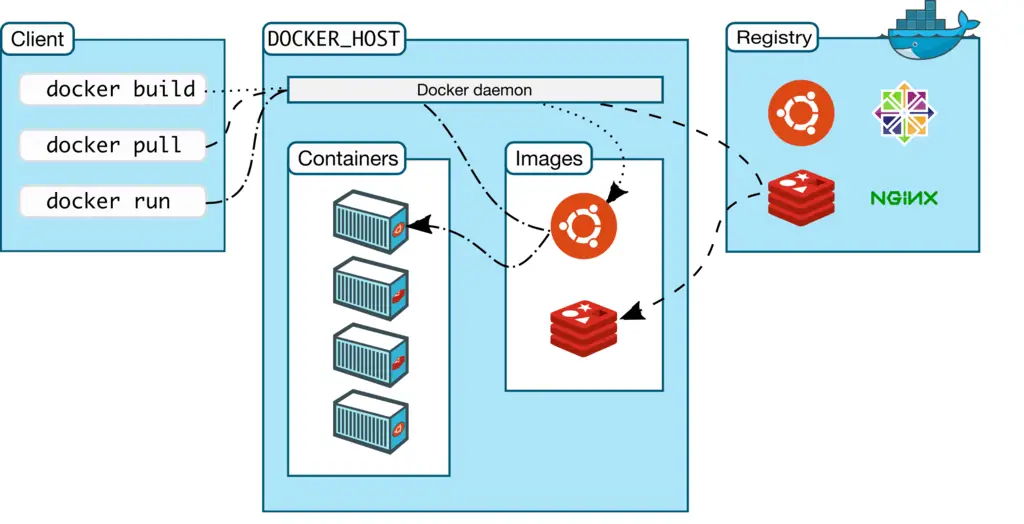
Docker internals itself isn’t magic
Leverages existing functionalities of the Linux kernel to provide its containerization capabilities.
Here’s a breakdown of the key components of docker internals at play:
1. Kernel Namespaces:
- Imagine namespaces as separate rooms in a house. Each Docker container gets its own set of namespaces, isolating its view of the system.
- PID Namespace: Isolates process IDs, so a container’s processes don’t interfere with the host system or other containers.
- UTS Namespace: Isolates hostname and domain name, allowing each container to have its own identity.
- Mount Namespace: This isolates the filesystem view, making each container see only its own mounted directories.
- Network Namespace (Optional): Provides network isolation, allowing containers to have their own network interfaces and IP addresses.
2. Control Groups (cgroups):
- Think of cgroups as resource managers for containers. They limit and control the amount of CPU, memory, disk I/O, and other resources a container can use. This ensures fair allocation and prevents containers from hogging resources.
3. Union File Systems:
- Docker images are built in layers, allowing for efficient storage. Union file systems combine these layers to create a single view for the container. This means changes made within a container only affect its top layer, leaving the base image layers untouched.
Here’s how docker internals together:
- Image Building: You define a Dockerfile with instructions on building the container’s environment. Each instruction creates a new layer in the image.
- Running a Container: When you run a container from an image, Docker:
- Creates namespaces, isolating the container’s processes, network, and filesystem view.
- Allocates resources through cgroups.
- Uses a union file system to layer the image’s filesystem on top of the host’s, providing a writable layer for the container.
- Container Execution: The application within the image is launched, running within the isolated environment with its allocated resources.
Docker internals is the combining namespaces, cgroups, and union file systems, Docker creates lightweight, portable containers that share the underlying host kernel. This allows you to efficiently package and run applications without worrying about conflicts or resource limitations.
Docker security involves securing the Docker daemon itself, the images you use, and the containers you run. Here are some key best practices to consider:
Docker Internals Daemon Security:
- Keep everything updated: Regularly update your Docker engine and the host kernel to patch vulnerabilities.
- Run Docker in rootless mode (if possible): This reduces the attack surface by limiting the privileges of the Docker daemon process.
- Secure the Docker socket: Restrict access to the Docker socket using Unix socket permissions or consider using a container runtime interface.
Docker Internals Image Security:
- Use trusted sources: Only use images from trusted publishers on Docker Hub or private registries.
- Scan for vulnerabilities: Regularly scan your images for vulnerabilities using vulnerability scanners.
- Minimize image size: Use minimal base images and avoid installing unnecessary packages to reduce the attack surface.
- Don’t store secrets in images: Use environment variables or a secrets management tool to store sensitive information.
- Practice least privilege: Ensure containers run as a non-root user and avoid using the
--privilegedflag unless absolutely necessary.
Docker Internals Container Security:
- Minimize exposed ports: Only expose the ports required for the container to function.
- Use read-only filesystems: When possible, mount the container’s filesystem in read-only mode.
- Resource limitations: Set resource limits (CPU, memory) to prevent containers from consuming excessive resources.
- Network isolation: Use separate Docker networks to isolate containers and prevent them from communicating with unintended hosts.
- Secure inter-container communication: Define how containers can communicate with each other using network policies.
- Logging and monitoring: Enable logging for containers and monitor for suspicious activity.
These are just some of the many Docker security best practices. For a more comprehensive list, you can refer to resources like the OWASP Docker Security Cheat Sheet https://cheatsheetseries.owasp.org/cheatsheets/Docker_Security_Cheat_Sheet.html or the Docker documentation on security best practices https://spacelift.io/blog/docker-security.
What you can do with a computer science degree?
Image credit
DaniloBarros, CC BY-SA 4.0, via Wikimedia Commons