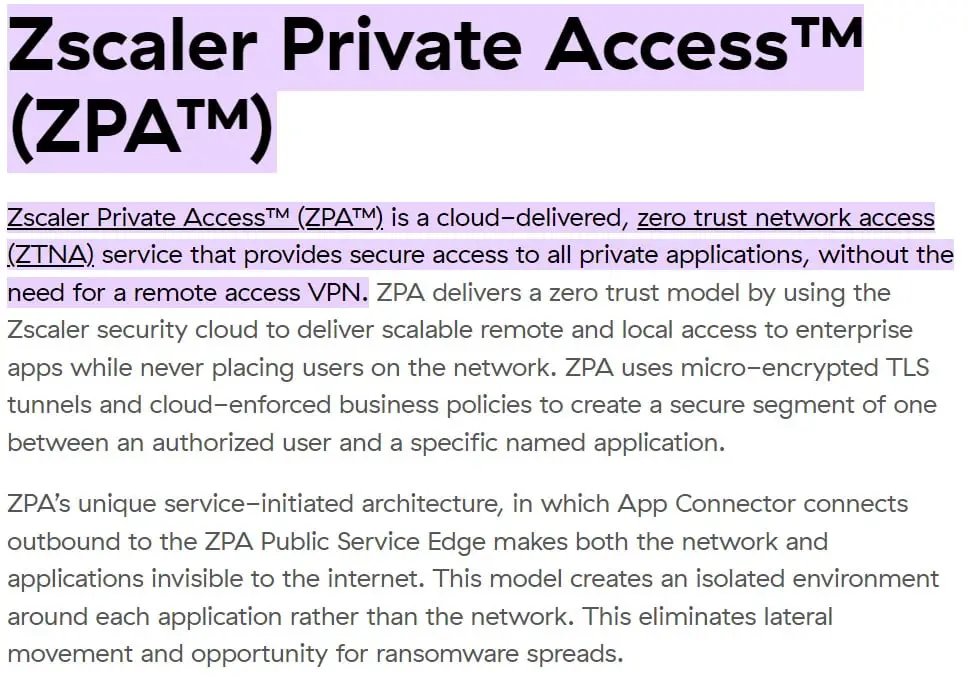
Zscaler Private Access (ZPA) for AWS DevOps Environments
Zscaler Private Access (ZPA) can be a secure and scalable solution for implementing VPN access to your AWS DevOps environment. Here’s a breakdown of the implementation process:
1. ZPA Configuration in AWS
- ZPA Client Connector: Install the ZPA client connector on Amazon EC2 instances or Amazon ECS container instances serving your DevOps tools. This connector establishes a secure tunnel between your instances and the ZPA cloud.
- Identity Integration: Integrate ZPA with your AWS identity provider (IdP) such as AWS IAM or Active Directory. This allows ZPA to leverage existing user credentials for access control.
- Policy Configuration: Define ZPA access policies to control which users and groups can access specific AWS resources or applications based on attributes like user role, device type, or location.
2. User Access and Workflows
- Zero Trust Access: Users will access AWS DevOps resources directly through a web browser without needing a traditional VPN client. ZPA handles authentication and authorization in the cloud, eliminating the need for complex network configurations.
- Seamless User Experience: Users can access AWS resources from any device with an internet connection, simplifying remote access for DevOps teams.
- Improved Security: ZPA enforces granular access controls and eliminates the need to expose entire subnets or resources to the public internet.
3. Additional Considerations
- AWS Services Access: ZPA can be configured to provide access to various AWS services like S3 buckets, CodeBuild instances, or CodePipeline stages.
- Multi-Factor Authentication (MFA): Implement MFA for an extra layer of security during the authentication process.
- Logging and Monitoring: Integrate ZPA with your existing logging and monitoring tools to track user access and identify potential security issues.
Benefits of using Zscaler ZPA for AWS DevOps:
- Improved Security: Zero Trust architecture reduces attack surface and enforces granular access control.
- Simplified Management: No need for complex network configurations or managing VPN clients.
- Scalability: ZPA can easily scale to accommodate a growing DevOps team.
- Remote Access: Enables secure access to AWS resources from anywhere with an internet connection.
Here are some additional resources for ZPA implementation with AWS:
- Zscaler Private Access Documentation: https://help.zscaler.com/zpa
- Zscaler for AWS DevOps Solutions: https://help.zscaler.com/zscaler-technology-partners/zscaler-and-azure-devops-deployment-guide
- AWS Zero Trust Architecture with ZPA: https://aws.amazon.com/security/zero-trust/
Remember, this is a general overview, and the specific implementation steps may vary depending on your AWS environment and DevOps workflow.
Here’s a breakdown of the key differences between traditional VPNs and cloud-based VPNs:
Deployment and Management:
- Traditional VPN: Requires hardware appliances like VPN concentrators to be installed and configured on-site. This can be complex and expensive, especially for geographically distributed teams. Management and maintenance are also an ongoing responsibility.
- Cloud-based VPN: Leverages the cloud infrastructure of a third-party provider. There’s no hardware to deploy or manage, simplifying setup and ongoing maintenance.
Scalability:
- Traditional VPN: Scaling a traditional VPN can be challenging. Adding new users or locations often requires additional hardware and configuration.
- Cloud-based VPN: Cloud-based VPNs are inherently scalable. They can easily accommodate growing user bases or geographically dispersed teams without additional infrastructure investment.
Security:
- Traditional VPN: Security depends on the strength of the on-site hardware and the expertise of the IT team managing it.
- Cloud-based VPN: Cloud providers constantly update their infrastructure and security measures to stay ahead of evolving threats. They may also offer additional security features like intrusion detection and prevention.
User Experience:
- Traditional VPN: Users may need to install and configure VPN software on their devices. Connecting to the VPN can sometimes be complex, especially for non-technical users.
- Cloud-based VPN: Cloud-based VPNs often offer easier user experiences. Users can connect through a web browser or a lightweight client with minimal configuration.
Cost:
- Traditional VPN: The upfront cost of hardware and ongoing maintenance can be significant, especially for small and medium-sized businesses.
- Cloud-based VPN: Cloud-based VPNs often have a subscription-based pricing model, which can be more cost-effective, especially for smaller organizations. However, costs can vary depending on data usage and the number of users.
Here’s a table summarizing the key differences:
| Feature | Traditional VPN | Cloud-based VPN |
|---|---|---|
| Deployment | On-premise hardware | Cloud infrastructure |
| Management | Complex, IT team responsibility | Simple, managed by provider |
| Scalability | Limited, requires additional hardware | Highly scalable |
| Security | Relies on on-premise security | Provider-managed security, often with additional features |
| User Experience | Can be complex | Simple, web browser or lightweight client |
| Cost | High upfront cost for hardware and maintenance | Subscription-based pricing, potentially lower overall cost |
Choosing the Right Option:
The best choice for your organization depends on your specific needs and resources. Here are some factors to consider:
- IT expertise: If you have a limited IT staff, a cloud-based VPN can simplify management.
- Scalability needs: If you anticipate a growing user base, a cloud-based VPN can be more cost-effective in the long run.
- Security requirements: Cloud providers often offer robust security features, but some organizations may have specific compliance requirements that necessitate an on-premise solution.
- Budget: Consider the upfront costs of hardware versus ongoing subscription fees for a cloud service.